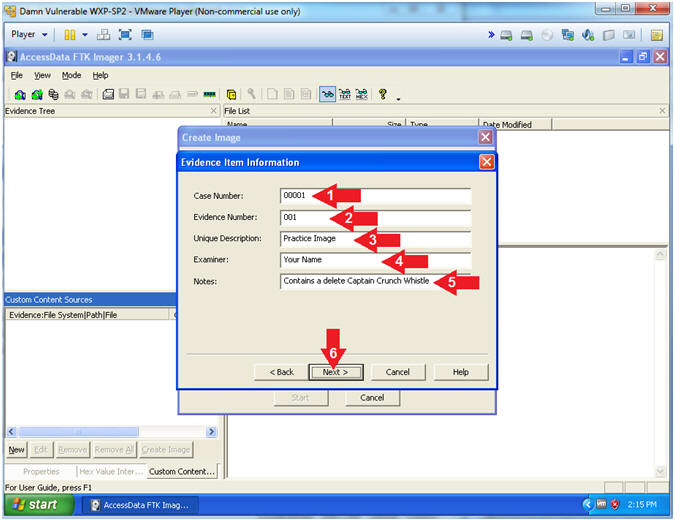
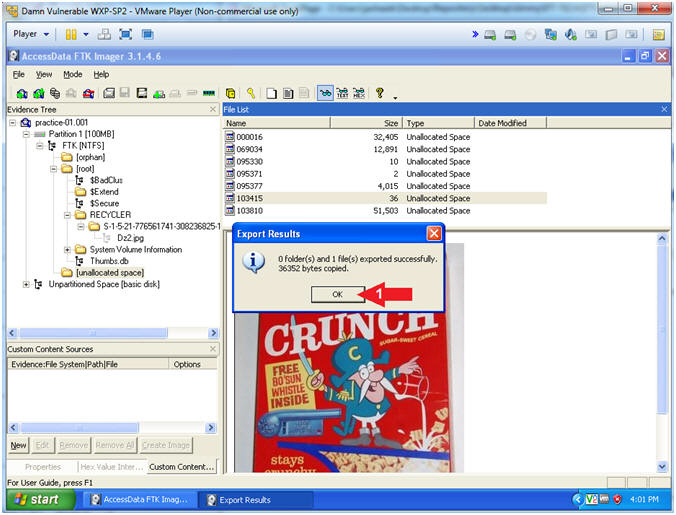
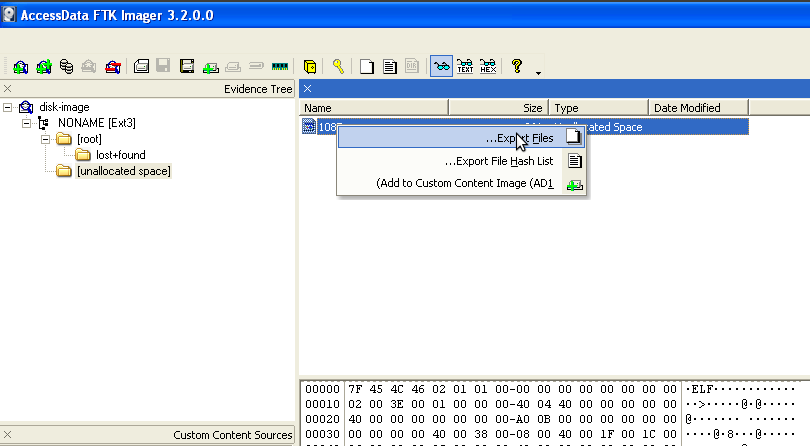
Computer Forensics with FTK [Fernando Carbone on Amazon. FREE shipping on qualifying offers. Written by a specialist in digital crime, this book helps you leverage the power of the FTK platform to conduct penetrating computer forensic investigations. With a stepbystep approach By selecting 'Yes' you are opting in to marketing email communications and consent to receive email communications regarding products, services and offerings from AccessData. , digital forensics ) is a very highly specialize area of Information Technology used to locate, copy, analyze, and document information present on electronic storage systems for presentation in a court of law. Order the Fluke Networks MS2100 MicroScanner2 Cable Verifier On Sale at Transcat. Forensic Toolkit FTK Imager is a forensics disk imaging software which scans the computer and digs out for various information. This free download is a standalone installer of Forensic Toolkit FTK Imager for Windows 32bit and 64bit. De verschillende tools staan hier per hoofdstuk gelinkt. Virtual PC Digital Forensics Forensic Toolkit (FTK ). Forensic Toolkit (FTK) version 6. Release Date: Nov 01, 2017 Download PageLearn More Forensic Toolkit (FTK) version 6. 2 EnCase Forensic is the global standard in digital investigation technology for forensic practitioners who need to conduct efficient, forensicallysound data collection and investigations using a repeatable and defensible process. Another way to verify that the partition is encrypted is to look for the on the Recovery partition. In fact, we are going to need this to decrypt the drive, so I am just going to export out this file while I have it opened in FTK Imager. Mount Image Pro mounts EnCase, FTK, DD, RAW, SMART, SafeBack, ISO, VMWare and other image files as a drive letter (or physical drive) on your computer. Chapter Contents Published: 12Mar15 at 09: 36: 48 Chapter 1 Introduction. FTK Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence. After you create an image of the data, use Forensic Toolkit (FTK) to perform a thorough forensic examination and create a report of your findings. GetData is a leading provider of end user software for data recovery, file recovery, computer forensics and file previewing. Our products are designed to get data back from computer hard drive, digital cameras, other storage media, and email files. Our software products available online, OEM, and in retail stores throughout the world. Since it is a custom piece of hardware I'm guessing it is using an open source filesystem. Burn an Ubuntu LiveCD, reboot your computer from it, then see if the CF card mounts. Today, cybersecurity professionals recognize that they can't possibly prevent every breach, but they can substantially reduce risk by quickly identifying and blocking breaches as they happen. Investigating The Cyber Breach: The Digital Forensics Guide for the Network Engineer is the first comprehensive guide to doing just that. The digital forensic process is a recognized scientific and forensic process used in digital forensics investigations. Forensics researcher Eoghan Casey defines it as a number of steps from the original incident alert through to reporting of findings. The process is predominantly used in computer and mobile forensic investigations and consists of three steps: acquisition, analysis and reporting..